SimulCrypt and BISS scrambling. Non-FPGA implementation principles
Introduction
Content encryption, more commonly referred to as “scrambling” in the DVB/IPTV context, is used to restrict access to subscription TV channels and video services.
Broadcasters, including satellite, cable, and IPTV providers, invest heavily in content production and procurement. Encryption allows them to monetize the content by selling subscriptions and controlling access. It creates a technical barrier that makes unauthorized copying and distribution of the signal pointless without the keys to decrypt it.
Today, encryption is also used in OTT services as well as in linear TV broadcasting (DVB and IPTV). In OTT, content protection is the responsibility of DRM systems such as Widevine, FairPlay, PlayReady, etc. They perform the same function as conditional access systems (CAS) in conventional broadcasting but represent a slightly different content distribution method and are therefore not considered in this article.
There are two main content protection methodologies used in DVB and IPTV broadcasting: SimulCrypt and BISS.
SimulCrypt: flexibility and scalability
SimulCrypt is the ETSI TS 103 197 specification that allows the use of one or more conditional access systems (CASs) for the same channel. Here, encryption keys are changed dynamically, and access rights are managed by the CAS which distributes the keys to the legitimate subscribers.
SimulCrypt requires an advanced infrastructure containing CAS servers, ECM/EMM generation, and multiplexer integration. However, it provides a high degree of reliability and flexibility by allowing the broadcaster to combine different CASs and customize the system according to specific business objectives.
BISS: simple solution for professional settings
BISS (Basic Interoperable Scrambling System) is a simpler, lightweight solution commonly used for temporary or service channels.
Its most basic version, BISS-1, uses a static key that remains unchanged for the entire duration of the broadcast. This simplifies setup by allowing manual key entry on both ends and makes for convenient signal transmission between TV companies or contractors as well as during live broadcasts.
However, if the key is leaked, the protection becomes ineffective because BISS-1 is essentially a “shared secret” system where the key is known to all participants. This scheme can only protect against accidental viewing but not an intentional attack.
The BISS-CA mode, which provided for dynamic key change, has not gained widespread acceptance. Therefore, the term BISS almost always refers in practice to the simplified BISS-1 version.
SimulCrypt/BISS coexistence
Both approaches are often used in parallel in modern networks.
SimulCrypt is used for secure broadcasting and end-user subscriptions, while BISS is employed for temporary and service channels where quick and simple setup is key.
Sometimes, BISS-1 is used to “protect” end-user content, but this scheme is extremely unreliable due to its static key which will eventually leak.
The primary purpose of scrambling is to prevent the unauthorized viewing and distribution of content. It is, however, important to realize that scrambling does not protect against content spoofing at the head-end station. If the spoofing is applied to the clear signal before it reaches the scrambler, the modified content will be readily encrypted and transmitted to subscribers. If it occurs after the scrambler, also in clear form, it will also likely succeed, because such a signal will enter subscriber receivers already decrypted.
How SimulCrypt works
The SimulCrypt architecture includes three key components—scrambler, multiplexer, and CAS—working in close cooperation.
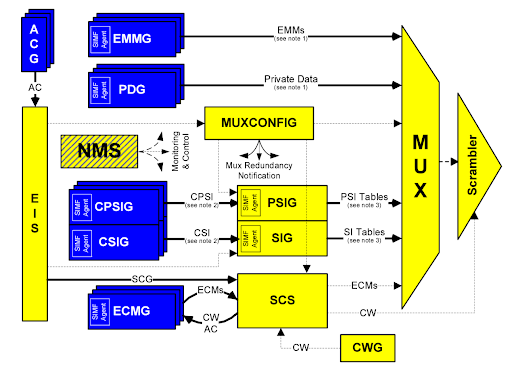
Fig. 1 - DVB SimulCrypt architecture
(from the ETSI TS 103 197 standard)
Main system components (see Fig. 1)
The blue blocks are components of the conditional access (CA) system:
- ACG (Access Criteria Generator): determines who is entitled to view the content
- EMMG (Entitlement Management Message Generator): generates entitlement management messages (EMMs) with access rights for subscribers
- ECMG (Entitlement Control Message Generator): creates entitlement control messages (ECMs) containing decoding keys (Control Words, or CW)
- PDG (Private Data Generator): generates service data (optional block)
- PDG, CPSIG, CSIG: generate additional CA system service information for PSI/SI
The yellow blocks are components of the multiplexer and scrambler:
- MUXCONFIG: controls multiplexer (MUX) settings but is almost never implemented in practice
- PSIG (Program Specific Information Generator): creates standard PSI tables (e.g., PAT/PMT)
- SIG (Service Information Generator): creates SI tables (e.g., SDT/EIT)
- SCG (Scrambling Control Group): controls the encryption process by defining which programs to protect with which keys
- CWG (Control Word Generator): generates encryption keys (Control Words)
- MUX (Multiplexer): combines all the streams (video, audio, PSI/SI, ECM, EMM) into a common MPEG-TS transport stream
- Scrambler: encrypts (scrambles) the transport stream using the CW keys
The CAS normally includes ECMG (Entitlement Control Message Generator) and EMMG (Entitlement Management Message Generator) servers that provide key generation and distribution as well as STB control. Examples of well-known CAS vendors include Verimatrix, Irdeto, and Secure TV.
Note that CAS implementations by different vendors can vary and do not always support all the functionality described in the specifications.
The Scrambler can be implemented as a separate program or hardware module. Scrambler implementations can vary significantly across different vendors and CASs but all of them encrypt the TS packet payload and set the associated bit in the Transport Scrambling Control (TSC) field of the TS packet header. This signals to the decoder that the packet is encrypted and requires a decryption key in order to be played back. A user attempting to play this stream without the keys will see a “black screen” or a distorted picture. In some implementations, the scrambler can be responsible for communicating with CAS by certain rules (the SimulCrypt protocol), receiving keys from it, and modifying the PSI/SI tables. In this case, the multiplexer may stay outside of the process altogether.
The multiplexer, in general, is integrated with the scrambler and inserts the ECM/EMMs received from the CAS into the stream and modifies the PSI/SI tables—for example, by adding a CAT table when an EMM is present and creating new PIDs in PMT for ECM, EMM, and CAT.
Encrypted DVB streams always contain ECMs and, occasionally, EMMs. In IPTV, it is more common to deliver EMMs using a separate bidirectional IP channel (out-of-band) at the request of the STB, therefore the main stream transmits only ECMs.
Encryption algorithms and their reliability
DVB and IPTV use the following main encryption algorithms: DVB-CSA1, DVB-CSA2, DVB-CSA3, CISSA (AES). They all have different key lengths and hence different computational complexity and strength. A license is required to use the DVB-CSA family of algorithms—something to consider when choosing a solution. Let us compare the above algorithms in a table.
Encryption algorithm | Key length (bits) | Strength | Computational complexity | Recommendation |
DVB-CSA1 | 48 (+16)* | Low | Low | Only for compatibility with the existing STB installed base |
DVB-CSA2 | 64 | Medium | Low | Recommended for new systems |
DVB-CSA3 | 128 | High | High | |
AES | 128 | High | High |
* The actual key length is 48 bits because only 48 of 64 are unique. Counting from 0, the 3rd and 7th bytes of the key will be a modulo-2 checksum of the previous 3 bytes.
In practice, DVB-CSA2 is considered as striking the optimum balance between security and performance. DVB-CSA1 is obsolete and not recommended. There are reports that it has been cracked, therefore the only reasonable use for it is to support the legacy installed base of subscriber devices. DVB-CSA3 is too computationally complex and provides no meaningful advantages, while the use of AES in linear broadcasting is limited to IPTV systems.
Features of the Elecard scrambler
As mentioned earlier, the specific scrambler implementation may vary across different vendors. Elecard’s solution, in addition to the standard scrambling functionality, offers additional capabilities that are useful in real-world scenarios.
- Selective encryption: e.g., only one of 16 TS packets is encrypted. This mode brings significant reduction in computational effort for both encryption and decryption, which is especially important for maintaining compatibility with the legacy installed base of relatively low-power STBs, while providing sufficient picture quality degradation when decoded without a key.

Fig. 2 - Selective encryption
Flexible stream selection: encrypt audio or video only.
ECMG connection loss behavior: backup is supported, and an action can be set for when backup ECMGs are not configured or unavailable, such as to continue encrypting with the last used key or suspend the protection temporarily.
EMM proxying: allows you to establish a single TCP connection to the EMMG and then multicast EMMs over the local network. The scrambler, in turn, can receive EMMs, both coming directly from the EMMG via TCP, and via multicast. This arrangement allows you to use fewer EMMG connections which are usually restricted in number by the license.
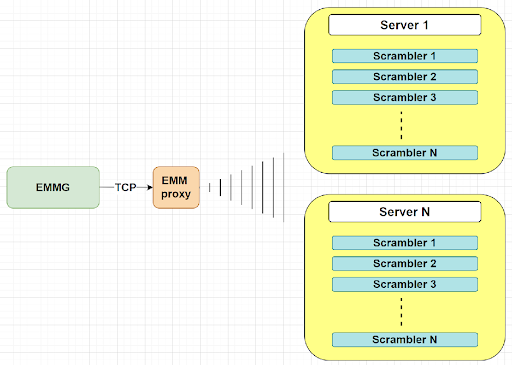
Fig. 3 - EMM proxying
Performance and eliminating the FPGA
The Elecard CodecWorks solution is entirely software-based and requires no specialized hardware.
Field-programmable gate arrays (FPGAs) offer high speed and energy efficiency but require specialized drivers, limiting the choice of platform and OS. In addition, they require a physical module to be installed in the server, one that must first be manufactured and supplied, which adds logistical complexity and reduces flexibility.
Elecard’s software-based scramblers run on any x86 servers, including virtual machines, and are updated using a conventional software patch. This is another undeniable advantage: updating the software solution is much easier and cheaper than replacing the device or even reflashing the firmware.
To achieve high performance without hardware accelerators, SIMD (AVX2) vector instructions are used which essentially perform several operations of the same type on several pieces of data at once. For more details about these, read our articles:
The AVX2 extension to the x86 instruction set that we use is supported even by Intel Haswell (2013+) and AMD Zen (2017+) CPUs.
The scramblers will also run on older CPUs that do not support AVX2, albeit with reduced performance.
For comparison, here is the encryption time for the same file with optimizations enabled and disabled:
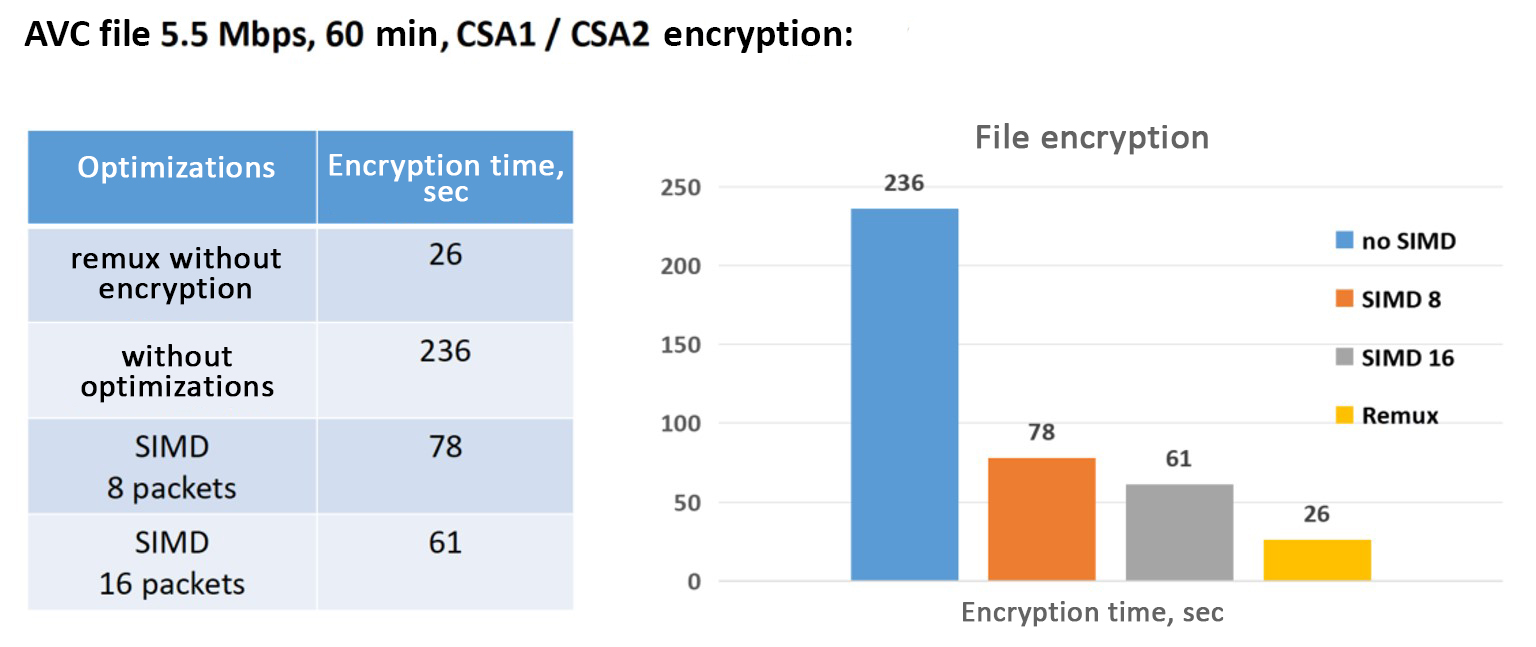
Fig. 4 - AVC-file
Or, with performance converted to Mbps per 1 CPU core:
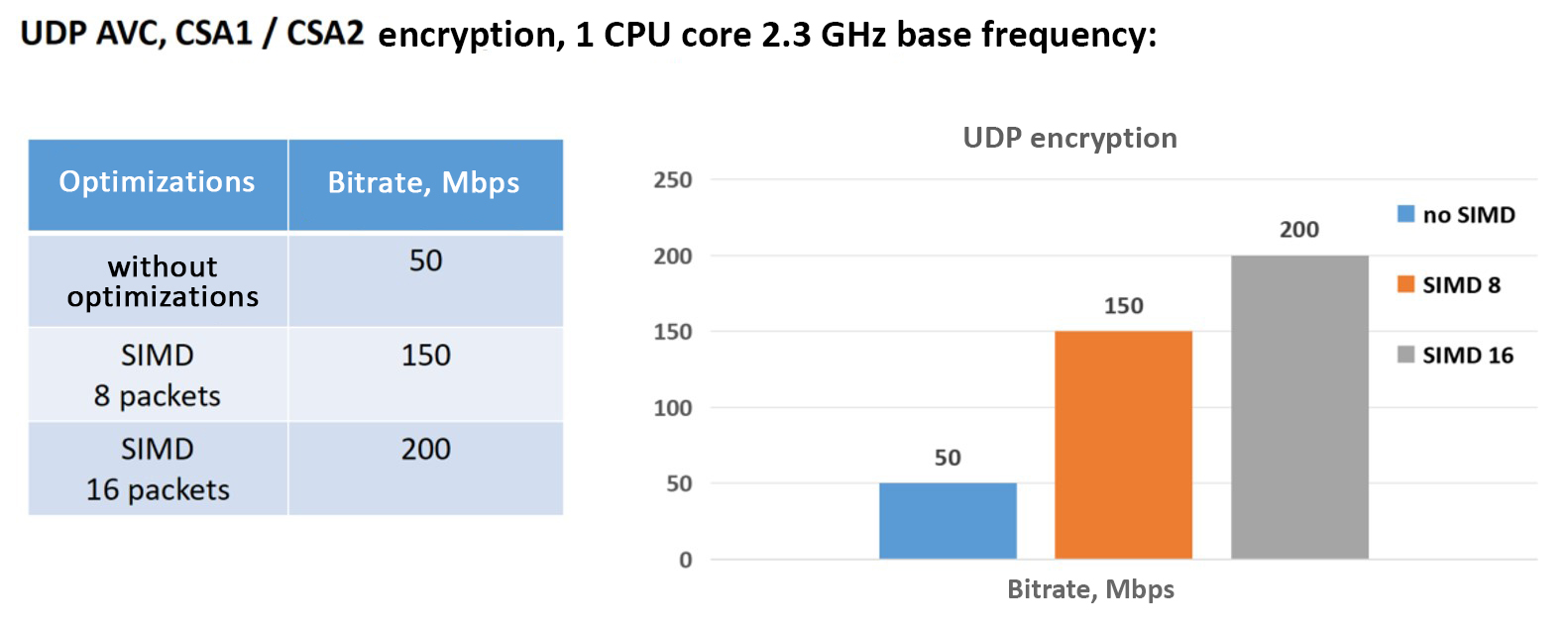
Fig. 5 - UDP AVC
In practical terms, this means that to achieve full scrambling of 20 MPTSs at an average bitrate of 100 Mbps each, a very modest server based on one Xeon Silver 4316 CPU (2.3 GHz, 20C/40T) will suffice:

Fig. 6 - CPU Intel server
Alternatively, you can consider AMD CPU-based systems (64 MPTSs at an average bitrate of 100 Mbps each):
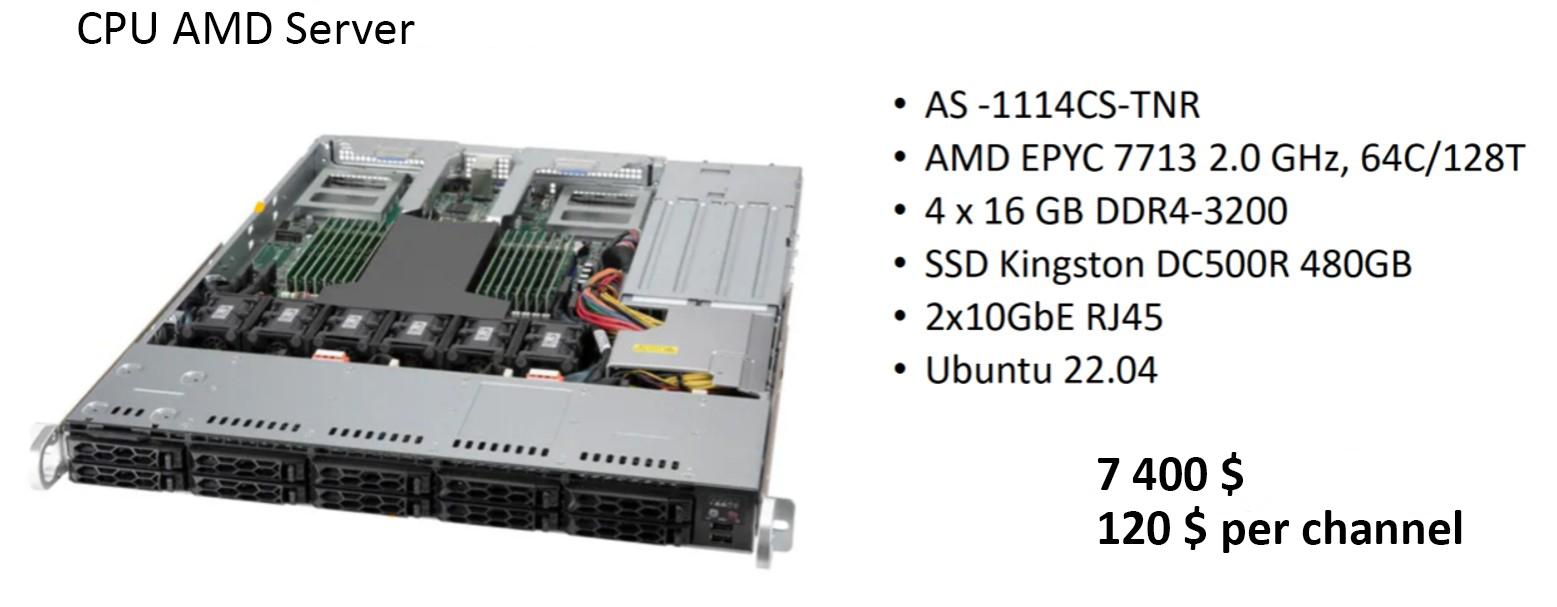
Fig. 7 - CPU AMD server
All your questions are welcome at sales@elecard.com
 Author
Author
Dmitriy Shmakov is a leading engineer at Elecard. He has been working in video analysis since 2021. Dmitriy is in charge of support of the Elecard's largest clients, such as Telstra, Globo, Amagi, Innet, etc.
28 october 2025